forked from vercel/next.js
-
Notifications
You must be signed in to change notification settings - Fork 0
[pull] canary from vercel:canary #218
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Merged
Merged
Conversation
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This PR fixes a small grammatical error in the Next.js rewrites documentation. <!-- Thanks for opening a PR! Your contribution is much appreciated. To make sure your PR is handled as smoothly as possible we request that you follow the checklist sections below. Choose the right checklist for the change(s) that you're making: ## For Contributors ### Improving Documentation - Run `pnpm prettier-fix` to fix formatting issues before opening the PR. - Read the Docs Contribution Guide to ensure your contribution follows the docs guidelines: https://nextjs.org/docs/community/contribution-guide ### Adding or Updating Examples - The "examples guidelines" are followed from our contributing doc https://github.com/vercel/next.js/blob/canary/contributing/examples/adding-examples.md - Make sure the linting passes by running `pnpm build && pnpm lint`. See https://github.com/vercel/next.js/blob/canary/contributing/repository/linting.md ### Fixing a bug - Related issues linked using `fixes #number` - Tests added. See: https://github.com/vercel/next.js/blob/canary/contributing/core/testing.md#writing-tests-for-nextjs - Errors have a helpful link attached, see https://github.com/vercel/next.js/blob/canary/contributing.md ### Adding a feature - Implements an existing feature request or RFC. Make sure the feature request has been accepted for implementation before opening a PR. (A discussion must be opened, see https://github.com/vercel/next.js/discussions/new?category=ideas) - Related issues/discussions are linked using `fixes #number` - e2e tests added (https://github.com/vercel/next.js/blob/canary/contributing/core/testing.md#writing-tests-for-nextjs) - Documentation added - Telemetry added. In case of a feature if it's used or not. - Errors have a helpful link attached, see https://github.com/vercel/next.js/blob/canary/contributing.md ## For Maintainers - Minimal description (aim for explaining to someone not on the team to understand the PR) - When linking to a Slack thread, you might want to share details of the conclusion - Link both the Linear (Fixes NEXT-xxx) and the GitHub issues - Add review comments if necessary to explain to the reviewer the logic behind a change ### What? ### Why? ### How? Closes NEXT- Fixes # --> --------- Co-authored-by: JJ Kasper <[email protected]>
### What? Add MCP for next dev exposing entrypoints, module graph and issues. Can be enabled via `NEXT_EXPERIMENTAL_MCP_SECRET=<random>` and makes the MCP available on `/_next/mcp?<random>`. Interesting change is in: packages/next/src/server/lib/router-utils/mcp.ts
### What? Show span name before attribute `name` in tracing when using custom named spans. Include category and original span name when grouping spans. Use more custom named spans.
### What? This fixes a bug where memory is not released back to the OS.
Fixes an issue with the x-nextjs-rewritten-query header where it responded without the dynamic parts of the URL filled in. For example, when rewriting to `/hello?id=123` to `/hello/123`: - Before: `x-nextjs-rewritten-query: id=__ESC_COLON_id` - After: `x-nextjs-rewritten-query: id=123`
…fixes #79059) (#81818) It's common in enterprise environments for employers to MITM all HTTPS traffic on employee machines to enforce network policies or to detect and block malware. For this to work, they install custom CA roots into the system store. Applications must read from this store. The default behavior of `reqwests` is to bundle the mozilla CA roots into the application, and only trust those. This is reasonable given some of the tradeoffs of the current rustls resolver implementations they use, but long-term it's better for most applications to just use the system CA store. This provides an opt-in experimental option for using the system CA store. We may use system CA certs by default in the future once seanmonstar/reqwest#2159 is resolved. Fixes #79059 Fixes #79060 ### Testing - Install [mitmproxy](https://docs.mitmproxy.org/stable/overview/installation/). - Install the generated mitmproxy CA cert to the system store: https://docs.mitmproxy.org/stable/concepts/certificates/ - Run `./mitmdump` (with no arguments) - Run an example app that uses google fonts: ``` pnpm pack-next --project ~/shadcn-ui/apps/v4 --no-js-build -- --release cd ~/shadcn-ui/apps/v4 pnpm i NEXT_TURBOPACK_EXPERIMENTAL_USE_SYSTEM_TLS_CERTS=0 HTTP_PROXY=localhost:8080 HTTPS_PROXY=localhost:8080 pnpm dev NEXT_TURBOPACK_EXPERIMENTAL_USE_SYSTEM_TLS_CERTS=1 HTTP_PROXY=localhost:8080 HTTPS_PROXY=localhost:8080 pnpm dev ``` When system TLS certs are disabled, we get warnings like this: ``` ⚠ [next]/internal/font/google/geist_mono_77f2790.module.css Error while requesting resource There was an issue establishing a connection while requesting https://fonts.googleapis.com/css2?family=Geist+Mono:wght@400&display=swap. Import trace: [next]/internal/font/google/geist_mono_77f2790.module.css [next]/internal/font/google/geist_mono_77f2790.js ./apps/v4/lib/fonts.ts ./apps/v4/app/layout.tsx ``` And mitmproxy shows the handshakes failing 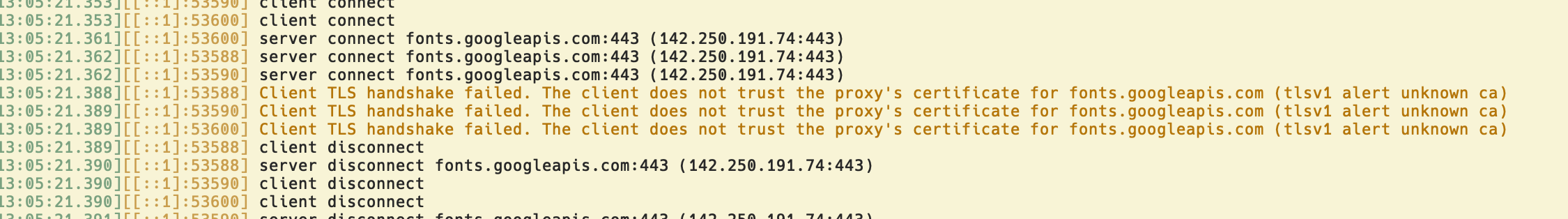 When system TLS certs are enabled, the app works.
Sign up for free
to subscribe to this conversation on GitHub.
Already have an account?
Sign in.
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
See Commits and Changes for more details.
Created by pull[bot] (v2.0.0-alpha.3)
pull[bot] (v2.0.0-alpha.3)
Can you help keep this open source service alive? 💖 Please sponsor : )